Official 2014 Latest Microsoft 70-414 Exam Dump Free Download(21-30)!
QUESTION 21
Your network contains two servers named Server1 and Server2 that run Windows Server 2012. Server1 and Server2 have the Hyper-V server role installed and are part of a host group named Group1 in Microsoft System Center 2012 Virtual Machine Manager (VMM). Server1 and Server2 have identical hardware, software, and settings. You configure VMM to migrate virtual machines if the CPU utilization on a host exceeds 65 percent. The current load on the servers is shown following table.
![clip_image001[5] clip_image001[5]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0015_thumb.jpg)
You start a new virtual machine on Server2 named VM8. VM8 has a CPU utilization of 20 percent. You discover that none of the virtual machines hosted on Server2 are migrated to Server1. You need to ensure that the virtual machines hosted on Server2 are migrated to Server1. What should you modify from the Dynamic Optimization configuration?
A. The Host Reserve threshold
B. The Aggressiveness level
C. The Dynamic Optimization threshold
D. The Power Optimization threshold
Answer: B
QUESTION 22
Your network contains a Microsoft System Center 2012 Virtual Machine Manager (VMM) server named Server1. You use Server1 to manage 20 Hyper-V hosts. The network also contains five Citrix XenServer visualization hosts. You need to recommend which installation is required to manage the XenServer servers from Server1. What should you recommend installing?
A. The Citrix XenServer – Microsoft System Center Integration Pack on Server1
B. Citrix Essentials for Hyper-V on Server1
C. Citrix Essentials for Hyper-V on the Citrix XenServer hosts
D. The Citrix XenServer – Microsoft System Center Integration Pack on the Citrix XenServer hosts
Answer: D
QUESTION 23
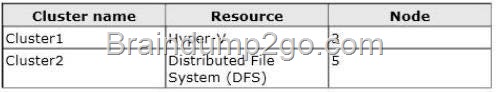
Your network contains two data centers named DataCenter1 and DataCenter2. The two data centers are connected by using a low-latency high-speed WAN link. Each data center contains multiple Hyper-V hosts that run Windows Server 2012. All servers connect to a Storage Area Network (SAN) in their local data center. You plan to implement 20 virtual machines that will be hosted on the Hyper- V hosts. You need to recommend a hosting solution for the virtual machines. The solution must meet the following requirements:
– Virtual machines must be available automatically on the network if a single Hyper-V host fails.
– Virtual machines must be available automatically on the network if a single data center fails.
What should you recommend?
A. One failover cluster and one Distributed File System (DFS) Replication group in each data center
B. One failover cluster in DataCenter1 and Hyper-V replicas to DataCenter2
C. One failover cluster that spans both data centers and SAN replication between the data centers
D. One failover cluster in DataCenter2 and one DFS Replication group in DataCenter1
Answer: C
QUESTION 24
You have a Hyper-V host named Hyper1 that has Windows Server 2012 Installed. Hyper1 hosts 20 virtual machines. Hyper1 has one physical network adapter. You need to implement a networking solution that evenly distributes the available bandwidth on Hyper1 to all of the virtual machines.
What should you modify?
A. The Quality of Service (QoS) Packet Scheduler settings of the physical network adapter
B. The settings of the network adapter
C. The settings of the virtual switch
D. The settings of the legacy network adapter
Answer: B
QUESTION 25
Your network contains an Active Directory domain named contoso.com. The domain contains a Microsoft System center 2012 infrastructure. You deploy a second System Center 2012 infrastructure in a test environment. You create a service template named Template1 in both System Center 2012 infrastructures. For self-service users, you create a service offering for Template1. The users create 20 instances of Template1. You modify Template1 in the test environment. You export the service template to a file named Templatel.xml. You need to ensure that the changes to Template1 can be applied to the existing instances in the production environment. What should you do when you import the template?
A. Create a new service template.
B. Overwrite the current service template.
C. Change the release number of the service template.
D. Change the name of the service template.
Answer: C
QUESTION 26
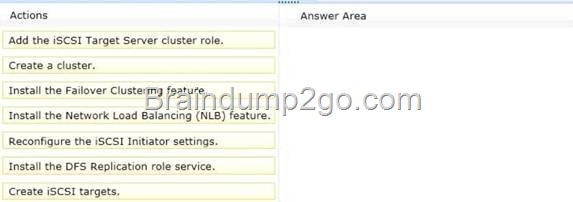
You plan to implement a virtualization solution to host 10 virtual machines. All of the virtual machines will be hosted on servers that run Windows Server 2012. You need to identify which servers must be deployed for the planned virtualization solution.
The solution must meet the following requirements:
– Minimize the number of servers.
– Ensure that live migration can be used between the hosts.
Which servers should you identify?
To answer, select the appropriate servers in the answer area.
![clip_image002[1] clip_image002[1]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0021_thumb.jpg)
Answer:
![clip_image002[3] clip_image002[3]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0023_thumb.jpg)
QUESTION 27
Your network contains an Active Directory domain named contoso.com. The corporate security policy states that when new user accounts, computer accounts, and contacts are added to an organizational unit (OU) named Secure, the addition must be audited. You need to recommend an auditing solution to meet the security policy. What should you include in the recommendation? (Each answer presents part of the solution. Choose all that apply.)
A. From the Default Domain Controllers Policy, enable the Audit directory services setting.
B. Create a new Group Policy object (GPO) that is linked to the Secure OU, and then modify the Audit directory
services setting.
C. From the Secure OU, modify the Auditing settings.
D. From the Default Domain Controllers Policy, enable the Audit object access setting.
E. From the Secure OU, modify the Permissions settings.
F. Create a new Group Policy object (GPO) that is linked to the Secure OU, and then modify the Audit object
access setting.
Answer: AB
Explanation:
* Creating a New Object: Resulting in multiple Event ID 5137 entries containing all attributes provided explicitly by the security principal that invoked the operation (but not those automatically generated by the system). Note that similar information also gets recorded if audit of User Account Management or Directory Service Access is enabled.
QUESTION 28
Your company has 10,000 users located in 25 different sites. All servers run Windows Server 2012. All client computers run either Windows 7 or Windows 8. You need to recommend a solution to provide self-service password reset for all of the users. What should you include in the recommendation?
A. the Microsoft System Center 2012 Service Manager Self-Service Portal and Microsoft System Center 2012
Operation Manager management packs
B. Microsoft System Center 2012 Operations Manager management packs and Microsoft System Center 2012
Configuration Manager collections
C. Microsoft System Center 2012 App Controller and Microsoft System Center 2012 Orchestrator runbooks
D. the Microsoft System Center 2012 Service Manager Self-Service Portal and Microsoft System Center 2012
Orchestrator runbooks
Answer: D
QUESTION 29
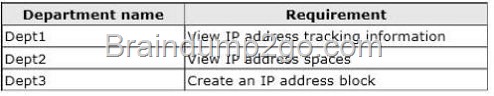
Your company has a human resources department, a finance department, a sales department, and an R&D department. The company audits the access of documents that contain department-specific sensitive information. You are planning an administrative model for the departments to meet the following requirements:
* Provide R&D managers with the ability to back up all the files of their department only.
* Provide finance managers with the ability to view the audit logs for the files of their department only.
* Provide human resources managers with the ability to view the audit logs for the files of their department only.
* Provide sales managers with the ability to modify the permissions on all the shared folders of their department only.
You need to identify the minimum amount of file servers required on the network to meet the requirements of each department.
How many file servers should you identify?
A. 1
B. 2
C. 3
D. 4
Answer: C
Explanation:
Finance managers & human resources (2 fileserver) need separate for sake of security. Sales managers R&D managers (1 fileserver) can work together (No contain sensitive information).
QUESTION 30
Your company has a main office and a branch office. Each office contains several hundred computers that run Windows 2012. You plan to deploy two Windows Server Update Services (WSUS) servers. The WSUS servers will be configured as shown in the following table.
![clip_image001[7] clip_image001[7]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0017_thumb.jpg)
You need to implement the WSUS infrastructure to meet the following requirements:
?All updates must be approved from a server in the main office. ?All client computers must connect to a WSUS server in their local office. What should you do? (Each correct answer presents part of the solution. Choose all that apply.)
A. Deploy a Group Policy object (GPO) that has the update location set to Server1.
B. On Server2, configure WSUS in Replica mode.
C. On Server1, configure WSUS in Replica mode.
D. On Server2, configure WSUS in Autonomous mode.
E. Deploy a Group Policy object (GPO) that has the update location set to Server2.
F. On Server1, configure WSUS in Autonomous mode.
Answer: ABEF
Explanation:
![clip_image002[5] clip_image002[5]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0025_thumb.jpg)
http://technet.microsoft.com/en-us/library/cc720448(v=ws.10).aspx
Passing Microsoft 70-414 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-414 Dump: http://www.braindump2go.com/70-414.html
![clip_image001[1] clip_image001[1]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0011_thumb.jpg)
![clip_image001[3] clip_image001[3]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0013_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0014_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0024_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00116_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00122_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/78cf42402b33_F447/clip_image00126_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00122_thumb.jpg)
![clip_image002[34] clip_image002[34]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00234_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00112_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00232_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00116_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00118_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00224_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00110_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00226_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00228_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image0024_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image0016_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image0028_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00210_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00212_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00214_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00216_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00218_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image00220_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/dc0341297668_A36E/clip_image0018_thumb.jpg)
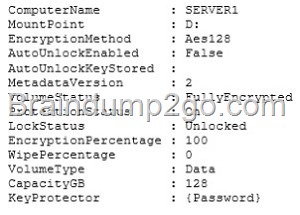
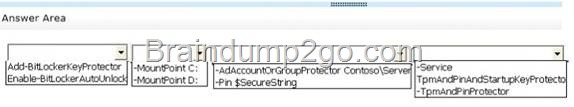
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-411-Ex_9B0B/clip_image0024_thumb.jpg)
![clip_image001[50] clip_image001[50]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00150_thumb.jpg)
![clip_image001[52] clip_image001[52]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00152_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00224_thumb.jpg)
![clip_image001[54] clip_image001[54]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00154_thumb.jpg)
![clip_image001[56] clip_image001[56]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00156_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00226_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00140_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00142_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00144_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00146_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00214_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00216_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00218_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00220_thumb.jpg)
![clip_image001[48] clip_image001[48]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00148_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00222_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00136_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00138_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image0026_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image0028_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00128_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00132_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00210_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00212_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00134_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00116_thumb.jpg)
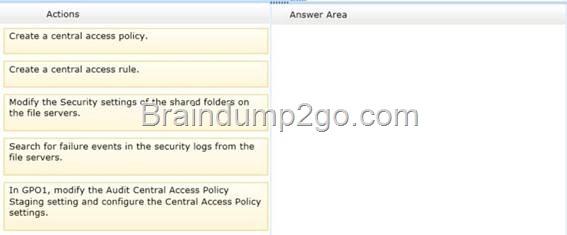
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image0024_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/4359f7ac92ab_77E7/clip_image00118_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00220_thumb.jpg)
![clip_image001[68] clip_image001[68]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00168_thumb.jpg)
![clip_image001[70] clip_image001[70]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00170_thumb.jpg)
![clip_image001[72] clip_image001[72]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00172_thumb.jpg)
![clip_image001[74] clip_image001[74]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00174_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00226_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00228_thumb.jpg)
![clip_image001[76] clip_image001[76]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00176_thumb.jpg)
![clip_image001[78] clip_image001[78]](http://examgod.com/l2pimages/cd84220663b7_9EF5/clip_image00178_thumb.jpg)