Official 2014 Latest Microsoft 70-412 Exam Dump Free Download(31-40)!
QUESTION 31
Your network contains three Active Directory forests. Each forest contains an Active Directory Rights Management Services (AD RMS) root cluster. All of the users in all of the forests must be able to access protected content from any of the forests. You need to identify the minimum number of AD RMS trusts required. How many trusts should you identify?
A. 2
B. 3
C. 4
D. 6
Answer: D
QUESTION 32
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. The domain contains a domain controller named DC1 that is configured as an enterprise root certification authority (CA). All users in the domain are issued a smart card and are required to log on to their domain-joined client computer by using their smart card. A user named User1 resigned and started to work for a competing company. You need to prevent User1 immediately from logging on to any computer in the domain. The solution must not prevent other users from logging on to the domain. Which tool should you use?
A. Active Directory Sites and Services
B. Active Directory Administrative Center
C. Server Manager
D. Certificate Templates
Answer: B
QUESTION 33
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DHCP Server server role installed. DHCP is configured as shown in the exhibit. (Click the Exhibit button.)
![clip_image001[54] clip_image001[54]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00154_thumb.jpg)
You discover that client computers cannot obtain IPv4 addresses from DC1. You need to ensure that the client computers can obtain IPv4 addresses from DC1. What should you do?
A. Activate the scope.
B. Authorize DC1.
C. Disable the Allow filters.
D. Disable the Deny filters.
Answer: C
Explanation:
There is no items in the deny List. So it means that client computers MAC addresses is not listed in the allow list. So we have to disable the “Allow Filters” http://technet.microsoft.com/en-us/library/ee956897(v=ws.10).aspx
![clip_image001[56] clip_image001[56]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00156_thumb.jpg)
QUESTION 34
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 and a domain controller named DC1. All servers run Windows Server 2012 R2. A Group Policy object (GPO) named GPO1 is linked to the domain. Server1 contains a folder named Folder1. Folder1 is shared as Share1. You need to ensure that authenticated users can request assistance when they are denied access to the resources on Server1. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Assign the Read Attributes NTFS permission on Folder1 to the Authenticated Users group.
B. Install the File Server Resource Manager role service on Server1.
C. Configure the Customize message for Access Denied errors policy setting of GPO1.
D. Enable the Enable access-denied assistance on client for all file types policy setting for GPO1.
E. Install the File Server Resource Manager role service on DC1.
Answer: BD
Explanation:
http://technet.microsoft.com/en-us/library/hh831402.aspx#BKMK_1
QUESTION 35
Your network contains an Active Directory domain named adatum.com. All domain controllers run Windows Server 2008 R2. The domain contains a file server named Server6 that runs Windows Server 2012 R2. Server6 contains a folder named Folder1. Folder1 is shared as Share1. The NTFS permissions on Folder1 are shown in the exhibit. (Click the Exhibit button.)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00226_thumb.jpg)
The domain contains two global groups named Group1 and Group2. You need to ensure that only users who are members of both Group1 and Group2 are denied access to Folder1. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Remove the Deny permission for Group1 from Folder1.
B. Deny Group2 permission to Folder1.
C. Install a domain controller that runs Windows Server 2012 R2.
D. Create a conditional expression.
E. Deny Group2 permission to Share1.
F. Deny Group1 permission to Share1.
Answer: CD
Explanation:
* Conditional Expressions for Permission Entries Windows Server 2008 R2 and Windows 7 enhanced Windows security descriptors by introducing a conditional access permission entry. Windows Server 2012 R2 takes advantage of conditional access permission entries by inserting user claims, device claims, and resource properties, into conditional expressions. Windows Server 2012 R2 security evaluates these expressions and allows or denies access based on results of the evaluation. Securing access to resources through claims is known as claims-based access control. Claims-based access control works with traditional access control to provide an additional layer of authorization that is flexible to the varying needs of the enterprise environment.
http://social.technet.microsoft.com/wiki/contents/articles/14269.introducing-dynamicaccess- control-en-us.aspx
QUESTION 36
Your network contains an Active Directory forest. The forest contains a single domain named contoso.com. The forest contains two Active Directory sites named Main and Branch1. The sites connect to each other by using a site link named Main-Branch1. There are no other site links. Each site contains several domain controllers. All domain controllers run Windows Server 2012 R2. Your company plans to open a new branch site named Branch2. The new site will have a WAN link that connects to the Main site only. The site will contain two domain controllers that run Windows Server 2012 R2. You need to create a new site and a new site link for Branch2. The solution must ensure that the domain controllers in Branch2 only replicate to the domain controllers in Branch1 if all of the domain controllers in Main are unavailable. Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00228_thumb.jpg)
Answer:
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00230_thumb.jpg)
QUESTION 37
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 has the DNS Server server role installed. The network contains client computers that run either Linux, Windows 7, or Windows 8. You have a standard primary zone named adatum.com as shown in the exhibit. (Click the Exhibit button.)
![clip_image001[58] clip_image001[58]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00158_thumb.jpg)
You plan to configure Name Protection on all of the DHCP servers. You need to configure the adatum.com zone to support Name Protection. Which two configurations should you perform from DNS Manager? (Each correct answer presents part of the solution. Choose two.)
A. Sign the zone.
B. Store the zone in Active Directory.
C. Modify the Security settings of the zone.
D. Configure Dynamic updates.
Answer: BD
Explanation:
http://technet.microsoft.com/en-us/library/ee941152(v=ws.10).aspx
![clip_image001[60] clip_image001[60]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00160_thumb.jpg)
QUESTION 38
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 have the Hyper-V server role installed. Server1 and Server2 are configured as Hyper-V replicas of each other. Server1 hosts a virtual machine named VM1. VM1 is replicated to Server2. You need to verify whether the replica of VM1 on Server2 is functional. The solution must ensure that VM1 remains accessible to clients. What should you do from Hyper-V Manager?
A. On Server1, execute a Planned Failover.
B. On Server1, execute a Test Failover.
C. On Server2, execute a Planned Failover.
D. On Server2, execute a Test Failover.
Answer: D
Explanation:
A. Server 1 is houses VM1 and it is replicated to Server2 – wrong server to failover and this is not a planned fail over case
B. Wrong server correct failover type
C. Wrong server, wrong failover type
D. Right server and failover type
http://blogs.technet.com/b/virtualization/archive/2012/07/31/types-of-failover-operations-inhyper- v-replica-partii-planned-failover.aspx
http://blogs.technet.com/b/virtualization/archive/2012/07/26/types-of-failover-operations-inhyper- v-replica.aspx
QUESTION 39
You have a failover cluster named Cluster1 that contains four nodes. All of the nodes run Windows Server 2012 R2. You need to force every node in Cluster1 to contact immediately the Windows Server Update Services (WSUS) server on your network for updates. Which tool should you use?
A. The Add-CauClusterRole cmdlet
B. The Wuauclt command
C. The Wusa command
D. The Invoke-CauScan cmdlet
Answer: D
Explanation:
A. Adds the Cluster-Aware Updating (CAU) clustered role that provides the self-updating functionality to the specified cluster.
B. the wuauclt utility allows you some control over the functioning of the Windows Update Agent C. The Wusa.exe file is in the %windir%\System32 folder. The Windows Update Standalone Installer uses the Windows Update Agent API to install update packages. Update packages have an .msu file name extension. The .msu file name extension is associated with the Windows Update Standalone Installer.
D. Performs a scan of cluster nodes for applicable updates and returns a list of the initial set of updates that would be applied to each node in a specified cluster. http://technet.microsoft.com/en-us/library/hh847235(v=wps.620).aspx http://technet.microsoft.com/en-us/library/cc720477(v=ws.10).aspx http://support.microsoft.com/kb/934307
http://technet.microsoft.com/en-us/library/hh847228(v=wps.620).aspx
![clip_image001[64] clip_image001[64]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00164_thumb.jpg)
QUESTION 40
Your network contains an Active Directory domain named contoso.com. The network contains a file server named Server1 that runs Windows Server 2012 R2. You are configuring a central access policy for temporary employees. You enable the Department resource property and assign the property a suggested value of Temp. You need to configure a target resource condition for the central access rule that is scoped to resources assigned to Temp only. Which condition should you use?
A. (Temp.Resource Equals “Department”)
B. (Resource.Temp Equals “Department”)
C. (Resource.Department Equals “Temp”)
D. (Department.Value Equals “Temp”)
Answer: C
Explanation:
http://technet.microsoft.com/fr-fr/library/hh846167.aspx
![clip_image001[66] clip_image001[66]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00166_thumb.jpg)
Passing Microsoft 70-412 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-411 Dump: http://www.braindump2go.com/70-412.html
![clip_image001[62] clip_image001[62]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00162_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00140_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00142_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00144_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00146_thumb.jpg)
![clip_image001[48] clip_image001[48]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00148_thumb.jpg)
![clip_image001[50] clip_image001[50]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00150_thumb.jpg)
![clip_image001[52] clip_image001[52]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00152_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00224_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00212_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00214_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00122_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00216_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00218_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00128_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00132_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00220_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00134_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00136_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00138_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00222_thumb.jpg)
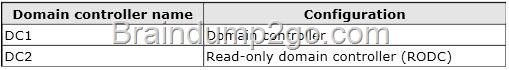
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image0016_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image0024_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image0018_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image0026_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00112_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image0028_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00116_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/a3b10f87ca43_7A5F/clip_image00120_thumb.jpg)
![clip_image001[100] clip_image001[100]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image001100_thumb.jpg)
![clip_image002[45] clip_image002[45]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00245_thumb.jpg)
![clip_image002[47] clip_image002[47]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00247_thumb.jpg)
![clip_image001[98] clip_image001[98]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00198_thumb.jpg)
![clip_image001[88] clip_image001[88]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00188_thumb.jpg)
![clip_image001[90] clip_image001[90]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00190_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00232_thumb.jpg)
![clip_image001[92] clip_image001[92]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00192_thumb.jpg)
![clip_image002[35] clip_image002[35]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00235_thumb.jpg)
![clip_image002[37] clip_image002[37]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00237_thumb.jpg)
![clip_image001[94] clip_image001[94]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00194_thumb.jpg)
![clip_image001[96] clip_image001[96]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00196_thumb.jpg)
![clip_image002[39] clip_image002[39]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00239_thumb.jpg)
![clip_image002[41] clip_image002[41]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00241_thumb.jpg)
![clip_image002[43] clip_image002[43]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00243_thumb.jpg)
![clip_image001[72] clip_image001[72]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00172_thumb.jpg)
![clip_image001[74] clip_image001[74]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00174_thumb.jpg)
![clip_image001[76] clip_image001[76]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00176_thumb.jpg)
![clip_image001[78] clip_image001[78]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00178_thumb.jpg)
![clip_image001[80] clip_image001[80]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00180_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00228_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00230_thumb.jpg)
![clip_image001[82] clip_image001[82]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00182_thumb.jpg)
![clip_image001[84] clip_image001[84]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00184_thumb.jpg)
![clip_image001[86] clip_image001[86]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00186_thumb.jpg)
![clip_image001[64] clip_image001[64]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00164_thumb.jpg)
![clip_image001[66] clip_image001[66]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00166_thumb.jpg)
![clip_image001[68] clip_image001[68]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00168_thumb.jpg)
![clip_image001[70] clip_image001[70]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00170_thumb.jpg)
![clip_image001[50] clip_image001[50]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00150_thumb.jpg)
![clip_image001[52] clip_image001[52]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00152_thumb.jpg)
![clip_image001[54] clip_image001[54]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00154_thumb.jpg)
![clip_image001[56] clip_image001[56]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00156_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00226_thumb.jpg)
![clip_image001[58] clip_image001[58]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00158_thumb.jpg)
![clip_image001[60] clip_image001[60]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00160_thumb.jpg)
![clip_image001[62] clip_image001[62]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00162_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00214_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00140_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00142_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00144_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00146_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00216_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00218_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00220_thumb.jpg)
![clip_image001[48] clip_image001[48]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00148_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00222_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00114_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image0026_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00116_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00128_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00132_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00134_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image0028_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00136_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00138_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00210_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image00212_thumb.jpg)
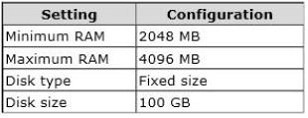
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image0024_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/894ac9351f42_79A5/clip_image0016_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/ca9d7143ff07_E5D2/clip_image0024_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/ca9d7143ff07_E5D2/clip_image0026_thumb.jpg)

![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/ca9d7143ff07_E5D2/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/ca9d7143ff07_E5D2/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/ca9d7143ff07_E5D2/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/ca9d7143ff07_E5D2/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/ca9d7143ff07_E5D2/clip_image00114_thumb.jpg)