Official 2014 Latest Microsoft 70-410 Exam Dump Free Download(231-240)!
QUESTION 231
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. Server1 runs Windows Server 2012 R2. Server2 runs Windows Server 2008 R2 Service Pack 1 (SP1) and has the DHCP Server server role installed. You need to manage DHCP on Server2 by using the DHCP console on Server1. What should you do first?
A. From Server Manager on Server2, enable Windows Remote Management.
B. From a command prompt on Server2, run winrm.exe.
C. From Server Manager on Server1, install a feature.
D. From the Microsoft Management Console on Server1, add a snap-in.
Answer: A
Explanation:
How do you enable remote management.
Assuming the remote server is all set up and prepared to enter production, first, open Server Manager on the remote server. Click on the “Configure Server Manager for Remote Management” link. Select the “Enable remote management of this server from other computers”. Click “Ok”.
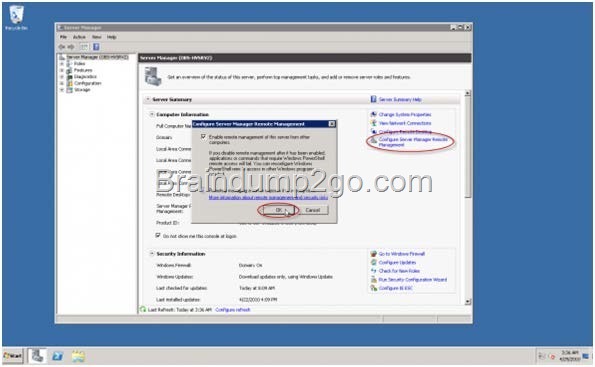
Note:
* You can use Server Manager to manage remote servers that are running Windows Server 2008 and Windows Server 2008 R2, but the following updates are required to fully manage these older operating systems.
/ Windows Management Framework 3.0
/ Performance Updates
* Windows Server 2008 R2, unlike Windows Server 2008 RTM, has a nice feature that allows you to remotely manage it, from another server or from a Windows 7 workstation, by using Server Manager.
* The tasks that you can perform remotely by using Server Manager include:
View Windows automatic updating status Run Best Practices Analyzer scans on roles.
View or change Windows Firewall information
View and manage roles
Manage installed services roles
View Internet Explorer Advanced Security Configuration settings (IE ESC) Configure Windows Error Reporting
View or change Windows Customer Experience Improvement Program (CEIP) status Reference: Configure Remote Management in Server Manager
QUESTION 232
Your network contains a production Active Directory forest named contoso.com and a test Active Directory forest named contoso.test. A trust relationship does not exist between the forests. In the contoso.test domain, you create a backup of a Group Policy object (GPO) named GPO1. You transfer the backup of GPO1 to a domain controller in the contoso.com domain. You need to create a GPO in contoso.com based on the settings of GPO1. You must achieve this goal by using the minimum amount of administrative effort. What should you do?
A. From Group Policy Management, right-click the Group Policy Objects container, and then click
Manage Backups.
B. From Group Policy Management, right-click the Starter GPOscontainer, and then click Manage Backups.
C. From Group Policy Management, create a new starter GPO. Right-click the new starter GPO, and then
click Restore from Backup.
D. From Group Policy Management, create a new GPO. Right-click the new GPO, and then click Import Settings.
E. From Windows PowerShell, run the Copy-GPOcmdlet and the Restore-GPOcmdlet.
F. From Windows PowerShell, run the New-GPOcmdlet and the Import-GPOcmdlet.
G. From Windows PowerShell, run the New-GPOcmdlet and the Restore-GPOcmdlet.
H. From Windows PowerShell, run the Get-GPOcmdlet and the Copy-GPOcmdlet.
Answer: DF
Explanation:
The New-GPO cmdlet creates a new GPO with a specified name. By default, the newly created GPO is notlinked to a site, domain, or organizational unit (OU). The Import-GPO cmdlet imports the settings from a GPO backup into a specified target GPO. The targetGPO can be in a different domain or forest than that from which the backup was made and it does nothave to exist prior to the operation. The Restore-GPO cmdlet restores a GPO backup to the original domain from which it was saved. If theoriginal domain is not available, or if the GPO no longer exists in the domain, the cmdlet fails.
http://technet.microsoft.com/en-us/library/cc781458(v=WS.10).aspx http://technet.microsoft.com/en-us/library/hh967461.aspx
http://technet.microsoft.com/en-us/library/ee461050.aspx
http://technet.microsoft.com/en-us/library/ee461044.aspx http://blogs.technet.com/b/askpfeplat/archive/2012/11/04/windows-server-2012-the-newand- improved-grouppolicy-management-console.aspx
QUESTION 233
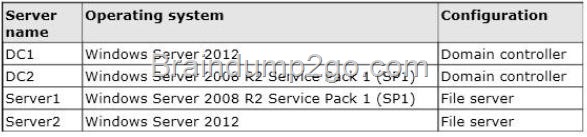
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You have received instructions to convert a basic disk to a GPT disk.
Which of the following is TRUE with regards to GPT disks? (Choose all that apply.)
A. To convert a basic disk to a GPT disk, the disk must not contain any partitions or volumes.
B. You can convert a basic disk to a GPT disk, regardless of partitions or volumes.
C. GPT is required for disks larger than 2 TB.
D. GPT is required for disks smaller than 2 TB.
E. The GPT partition style can be used on removable media.
F. GPT disks make use of the standard BIOS partition table.
Answer: AC
Explanation:
A. For a drive to be eligible for conversion to dynamic, all basic data partitions on the drive must be contiguous
C. GPT allows a much larger partition size greater than 2 terabytes (TB) D. 2 terabytes is the limit for MBR disks.
E. Dynamic disks are not supported on portable computers, removable disks, detachable disks that use USB or IEEE 1394 interfaces
F. Windows only supports booting from a GPT disk on systems that contain Unified Extensible Firmware Interface (UEFI) boot firmware.
Master boot record (MBR) disks use the standard BIOS partition table. GUID partition table (GPT) disks use unified extensible firmware interface (UEFI). One advantage of GPT disks is that you can have more than four partitions on each disk. GPT is also required for disks larger than 2 terabytes.
Portable computers and removable media. Dynamic disks are not supported on portable computers, removable disks, detachable disks that use Universal Serial Bus (USB) or IEEE 1394 (also called FireWire) interfaces, or on disks connected to shared SCSI buses. If you are using a portable computer and right-click a disk in the graphical or list view in Disk Management, you will not see the option to convert the disk to dynamic.
Dynamic disks are a separate form of volume management that allows volumes to have noncontiguous extents on one or more physical disks. Dynamic disks and volumes rely on the Logical Disk Manager (LDM) and Virtual Disk Service (VDS) and their associated features. These features enable you to perform tasks such as converting basic disks into dynamic disks, and creating fault-tolerant volumes. To encourage the use of dynamic disks, multi-partition volume support was removed from basic disks, and is now exclusively supported on dynamic disks. GPT disks can be converted to MBR disks only if all existing partitioning is first deleted, with associated loss of data.
Q. What happens when a basic disk is converted to dynamic?
A. For a drive to be eligible for conversion to dynamic, all basic data partitions on the drive must be contiguous. If other unrecognized partitions separate basic data partitions, the disk cannot be converted. This is one of the reasons that the MSR must be created before any basic data partitions. The first step in conversion is to separate a portion of the MSR to create the configuration database partition. All non-bootable basic partitions are then combined into a single data container partition. Boot partitions are retained as separate data container partitions. This is analogous to conversion of primary partitions.
Windows XP and later versions of the Windows operating system differs from Windows 2000 in that basic and extended partitions are preferentially converted to a single 0x42 partition, rather than being retained as multiple distinct 0x42 partitions as on Windows 2000.
http://technet.microsoft.com/en-us/library/cc725671.aspx
http://msdn.microsoft.com/en-us/library/windows/desktop/aa363785%28v=vs.85%29.aspx http://msdn.microsoft.com/en-us/library/windows/hardware/gg463525.aspx http://technet.microsoft.com/en-us/library/cc757696.aspx
http://technet.microsoft.com/en-us/library/cc776315.aspx
QUESTION 234
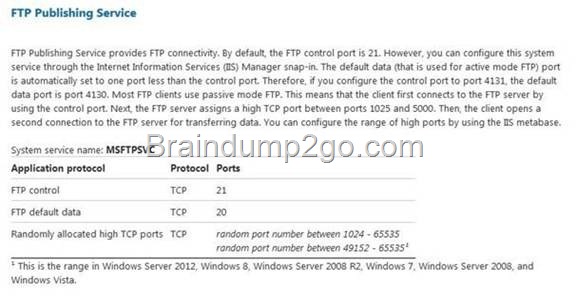
Server1 runs Windows Server 2012 R2 and is installed as an FTP server. Client use App1 to connect to Server1 for FTP. App1 use TCP port 21 for control and a dynamic port for data. You have allowed port 21 in firewall. What youshould next do to allow clients to use App1 to connect to server1 using ftp.
A. At Server1 allow firewall rule of outbound
B. At Server1 allow firewall rule of inbound
C. Netsh advfirewalldomainprofile state off
D. Netsh advfirewall set global StatefulFtp enable
Answer: D
Explanation:
Set global statefulftp
Configures how Windows Firewall with Advanced Security handles FTP traffic that uses an initial connection onone port to request a data connection on a different port. This affects both active and passive FTP.
http://technet.microsoft.com/en-us/library/cc771920%28v=ws.10%29.aspx http://support.microsoft.com/kb/832017/en-us#method20
QUESTION 235
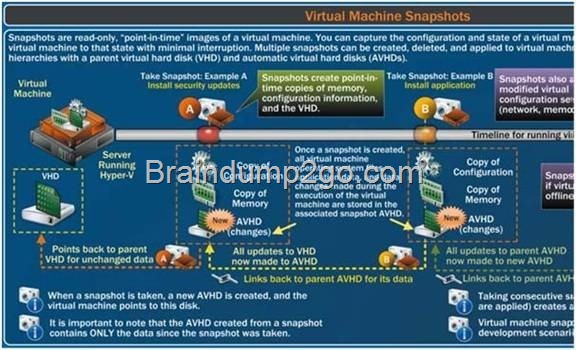
You have a server named Server1 that runs Windows Server 2012 R2. You plan to enable Hyper-V Network Visualization on Server1. You need to install the Windows Network Virtualization Filter Driver on Server1. Which Windows PowerShell cmdlet should you run?
A. Set-NetVirtualizationGlobal
B. Set-NetAdapterVmq
C. Add-WindowsFeature
D. Enable-NetAdapterBinding
Answer: D
QUESTION 236
A company has a forest with 4 sites. Subnets are as follows:
– MainOffice 172.16.1.0 Subnet: 255.255.255.0 Gateway 172.16.1.254
– Site1 192.168.12.0 Subnet: 255.255.255.0
– Site 2 192.168.13.0 Subnet: 255.255.255.0
– Site 3 192.168.14.0 Subnet: 255.255.255.0
– Site 4 192.168.15.0 Subnet: 255.255.255.0
You add a new server to the MainOffice and it needs to be able to communicate to all sites.
Which route command would you run?
A. route add -p 192.168.8.0 netmask 255.255.252.0 172.16.1.254
B. route add -p 192.168.0.0 netmask 255.255.248.0 172.16.1.254
C. route add -p 192.168.12.0 netmask 255.255.252.0 172.16.1.254
D. route add -p 192.168.12.0 netmask 255.255.240.0 172.16.1.254
Answer: C
QUESTION 237
Server 1 and Server2 host a load-balanced Application pool named AppPool1. You need to ensure thatAppPool1 uses a group Managed Service Account as its identity. Which 3 actions should you perform?
A. Install a domain controller that runs Windows Server 2012 R2, Run the New- ADServiceAccountcmdlet,
Modify the settings of AppPool1.
B. Configure the Security settings of the contoso.com zone.
C. Add a second legacy network adapter, and then run the Set-VMNetworkAdoptercmdlet.
D. From Windows Powershell, run Get-DNSServerDiagnostics.
Answer: A
Explanation:
For the application pool to use a group Managed Service account as its identity you will have to make sure that there is a domain controller where you can add the account and then modify the application pool accordingly. Thus you should use the New- ADServiceAccount on the domain controller that will create a new Active Directory service account.
QUESTION 238
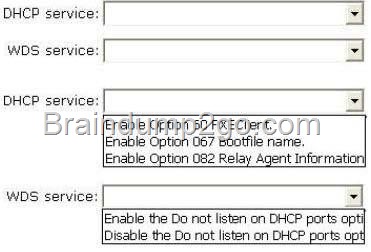
Hotspot Question
You run a Windows Server 2012 R2and implementing 3 new printers in a warehouse. You need to makean exclusion forthese IP addresses within DHCP server. Select the location where would configure at the DHCP console?
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0014_thumb.jpg)
Answer:
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0016_thumb.jpg)
Explanation:
http://technet.microsoft.com/en-us/library/cc737978%28v=ws.10%29.aspx
QUESTION 239
Hotspot Question
You have a Server Core 2012 installation and all roles and features removed. The server does not haveaccess to Windows Update. You mount the network volume containing the installation files for Server 2012. You need to install DNS and DHCP server role. Which directory do you reference for installing?
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0018_thumb.jpg)
Answer:
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00110_thumb.jpg)
Explanation:
http://blogs.technet.com/b/askpfeplat/archive/2013/02/24/how-to-reduce-the-size-of-the-winsxs-directory- and-free-up-disk-space-on-windows-server-2012-using-features-on-demand.aspx
QUESTION 240
Server1 runs Windows Server 2012 R2 and is installed as an FTP server. Client use App1 to connect to Server1 for FTP. App1 use TCP port 21 for control and a dynamic port for data. You have allowed port 21 in firewall. What youshould next do to allow clients to use App1 to connect to server1 using ftp.
A. At Server1 allow firewall rule of outbound
B. At Server1 allow firewall rule of inbound
C. netshadvfirewalldomainprofile state off
D. netshadvfirewall set global StatefulFtp enable
Answer: D
Explanation:
Set global statefulftp Configures how Windows Firewall with Advanced Security handles FTP traffic that uses an initial connection onone port to request a data connection on a different port. This affects both active and passive FTP.
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0024_thumb.jpg)
http://technet.microsoft.com/en-us/library/cc771920%28v=ws.10%29.aspx http://support.microsoft.com/kb/832017/en-us#method20
Passing Microsoft 70-410 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-410 Dump:
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb_5.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb_5.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb_5.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb_5.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb_5.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00114_thumb_4.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb_5.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb_5.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00124_thumb_3.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb_4.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0028_thumb_4.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00210_thumb_3.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00212_thumb_3.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00214_thumb_3.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00126_thumb_3.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb_4.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb_4.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb_4.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb_4.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb_4.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00114_thumb_3.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00116_thumb_3.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00118_thumb_3.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00120_thumb_3.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb_4.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00122_thumb_3.jpg)

![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb_3.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb_3.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb_3.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb_3.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb_3.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb_3.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb_3.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0028_thumb_3.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00132_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00228_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00232_thumb.jpg)
![clip_image002[34] clip_image002[34]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00234_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00134_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00136_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00236_thumb.jpg)
![clip_image002[38] clip_image002[38]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00238_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00138_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00140_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00142_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00144_thumb.jpg)
![clip_image002[40] clip_image002[40]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00240_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00146_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00120_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00220_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00226_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00128_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0028_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00210_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00212_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00214_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00216_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00116_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00218_thumb.jpg)
![clip_image001[54] clip_image001[54]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00154_thumb.jpg)
![clip_image002[46] clip_image002[46]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00246_thumb.jpg)
![clip_image001[56] clip_image001[56]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00156_thumb.jpg)
![clip_image001[58] clip_image001[58]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00158_thumb.jpg)
![clip_image001[60] clip_image001[60]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00160_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00144_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00146_thumb.jpg)
![clip_image001[48] clip_image001[48]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00148_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00232_thumb.jpg)
![clip_image002[34] clip_image002[34]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00234_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00236_thumb.jpg)
![clip_image002[38] clip_image002[38]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00238_thumb.jpg)
![clip_image002[40] clip_image002[40]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00240_thumb.jpg)
![clip_image002[42] clip_image002[42]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00242_thumb.jpg)
![clip_image002[44] clip_image002[44]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00244_thumb.jpg)
![clip_image001[50] clip_image001[50]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00150_thumb.jpg)
![clip_image001[52] clip_image001[52]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00152_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00134_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00136_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00138_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00226_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00140_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00228_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00142_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00120_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00212_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00124_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00214_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00216_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00126_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00218_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00220_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00224_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00128_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00132_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image0024_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image0018_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image0026_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image0028_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00110_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00210_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00116_thumb.jpg)
![clip_image001[17] clip_image001[17]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image00117_thumb.jpg)
![clip_image001[19] clip_image001[19]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image00119_thumb.jpg)